Endpoint Security Starts with Endpoint VisibilityPromisec Team
14 Jun, 2021 · 3 minutes
Could 60% of IT leaders be wrong?
As time goes by, hackers have become increasingly sophisticated. IT departments rightly pursue cybersecurity innovations to keep their organizations safe, implementing advanced – and expensive! – cybersecurity tools. However, there’s a pretty surprising statistic which seems more elementary than using complicated tools. And it’s this – 60% of breaches could be avoided simply by installing patches.
According to a survey of 3,000 security professionals in nine countries, “60% of breaches were linked to a vulnerability where a patch was available, but not applied,” reports Security Boulevard.
Of course, for many IT departments, staying up to date on all endpoints isn’t as easy as it sounds.
In fact, when “Illumio surveyed IT professionals at 344 mid- to large-sized corporations,” it “found that… 59% of respondents are unable to see attempted connections to work laptops from other devices on the local home network,” the company reported.
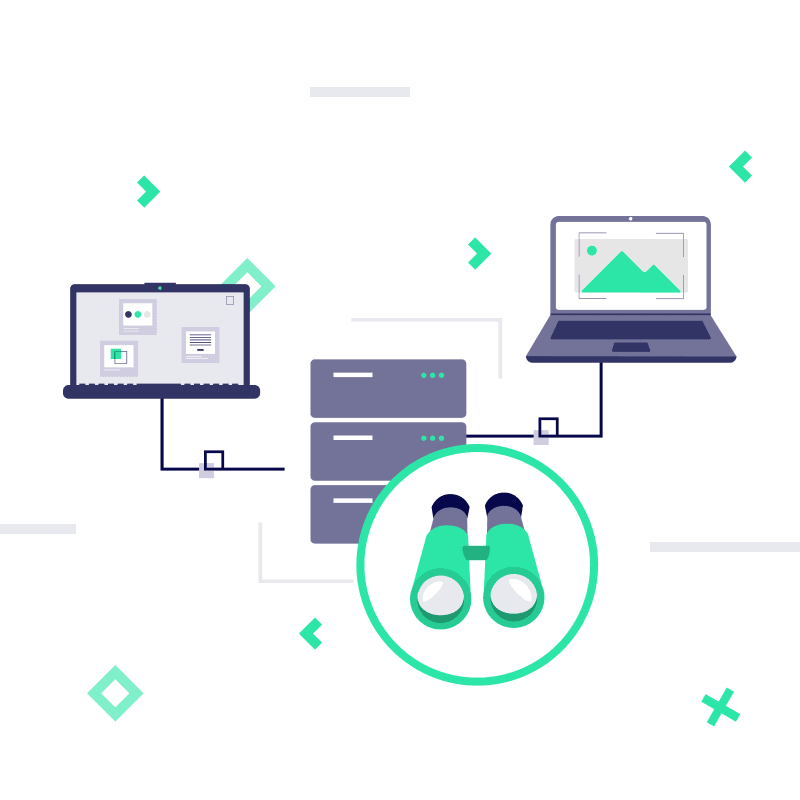
And you can’t change what you can’t see.
The Most Important Foundation of Cybersecurity and IT Management
When you have visibility into all your endpoints and server activities, you:
=> Know exactly what employees do with corporate equipment and data. Are they using unauthorized apps? Sharing files they shouldn’t? Have they forgotten to turn on or update their antivirus?
=> Get more control over what they can do with them. Once you define how corporate equipment and data should actually be used, you can tap into a variety of resources such as monitoring and advanced software tools, allowing you to regain control.
=> Take action immediately when something isn’t right. Decide on a policy execution strategy. In some cases, the best solution is to contact the employee and educate them on why certain actions might put the organization at risk. Other times, you’ll want the ability to take action remotely, like disabling an infected device from your overall network until you can ensure it’s safe again.
Combine IT Visibility with Practical and Simple Remediation, and Hackers Won’t Stand a Chance
Of course, to prove the value of your IT investments, prioritize tools and strategies that simplify taking action once visibility has been established.
=> Detect and correct incompliant actions in your organization. As mentioned above, this can be done by IT, combining detection tools with employee training.
=> Remediate emerging risks before they cause damage. Once you gain visibility, you can be notified when there are small deviations from your policy, and fix them proactively rather than waiting to find out just a little too late.
=> Use the data you gain to optimize your current investment. Easily prove ROI and the direct value of your IT department to the company’s bottom line by demonstrating meeting compliance and enforcing security policies. As your organization grows and your network becomes more complex, visibility becomes mandatory and an essential tool to enable the continued operation of your systems.
In a nutshell, this is how you’ll gain control over what your employees are doing with their corporate workstations, and over the security of your endpoints.
Get (Free) Endpoint Visibility Guidance from Cybersecurity Experts
Promisec is bringing together some of the top cybersecurity experts – including Ori Shahar – to talk about best practices for better endpoint visibility. Join the webinar here on June 23 at 9:00 AM ET, and you’ll be able to ask them your burning questions.
Sign up for the newsletter
If you want relevant updates occasionally, sign up for the private newsletter. Your email is never shared.